Forensics Beginner Challenges Part 2 of 3
- Jorge Morán
- Ctf , Forensics
- March 22, 2024
- 9 min
Let’s start the second installment of this series about solving forensics beginner challenges. If you haven’t, please visit part 1 . We’ll continue using this repo.
Challenge 6
This challenge provides a file called verbs_dict.txt. If we open it, we’ll eventually find the flag. It’s there in plaintext. However, if we want to be more methodical, we can search for it. To do so, we’ll use grep with the -o flag so that it only provides the matching text, and the -P flag to include a nice regular expression.
Let’s execute the command
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/06_long_words]
└─$ cat verbs_dict.txt | grep -o -P '.{0,3}cercCTF.{0,40}'
te cercCTF{l0ng_do5nt_m4tter_f0r_pro0szz} share pa
The regular expression we used provides three additional characters before ceroCTF and 40 characters after that matching text. Even though we are printing text beyond the flag, it’s more than enough to find what we need.
The flag is: cercCTF{l0ng_do5nt_m4tter_f0r_pro0szz}
Challenge 7
Challenge 7 is called “so deep”, and provides a file called file.zip. If we unzip it, we’ll find a long list of directories
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/07_so_deep]
└─$ unzip file.zip
...
extracting: 69/gmmbsfmydd
extracting: 69/oho7n4vkqf
extracting: 69/9wyv7mz80y
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/07_so_deep]
└─$ ls
0 101 105 109 112 13 17 20 24 28 31 35 39 42 46 5 53 57 60 64 68
1 102 106 11 113 14 18 21 25 29 32 36 4 43 47 50 54 58 61 65 69
10 103 107 110 114 15 19 22 26 3 33 37 40 44 48 51 55 59 62 66 file.zip
100 104 108 111 12 16 2 23 27 30 34 38 41 45 49 52 56 6 63 67
After unzipping the file, we now have many directories, and there are files in all of those directories. So, this time we are going to use a similar trick as the one we used for challenge 6. We’ll use the find command to get a reference to all the files, and we’ll grep for the flag in every file until we find it. This sounds more complicated than what it is. Let’s do it.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/07_so_deep]
└─$ find . -type f | xargs grep -o -P 'cercCTF.{0,28}'
./49/jou1yi8awe:cercCTF{d33p_and_d1ve_fruuee33lyyi}
Now we know that the flag is in the ./49/jou1yi8awe file, and we have the value. It’s worth noting that we could have also used a grep without the find command. To do it that way, we only needed to add the -R flag so that it searches recursively.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/07_so_deep]
└─$ grep -R -o -P 'cercCTF.{0,28}'
49/jou1yi8awe:cercCTF{d33p_and_d1ve_fruuee33lyyi}
The flag is: cercCTF{d33p_and_d1ve_fruuee33lyyi}
Challenge 8
From this point forward, let’s make a note of every challenge name, as they provide clues about what to do. Challenge 8 is called head, and the file it provides is a seemingly broken image called image.png. Let’s use the same methodology of previous exercises to try and understand what we are facing. First, we’ll use the file command and then binwalk and compare their results.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/08_head]
└─$ file image.png
image.png: data
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/08_head]
└─$ binwalk image.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
62 0x3E Zlib compressed data, compressed
Unfortunately, the results we are getting are not consistent with one another. Let’s add another tool to our arsenal. When we are doing forensic analyses, hex editors and viewers are our friends. For this exercise, we’ll use Okteta. If we don’t already have it, we can install it in Kali with the following command.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/08_head]
└─$ sudo apt update && sudo apt install -y okteta
Now that we have the app, let’s proceed to open the app and load our file.
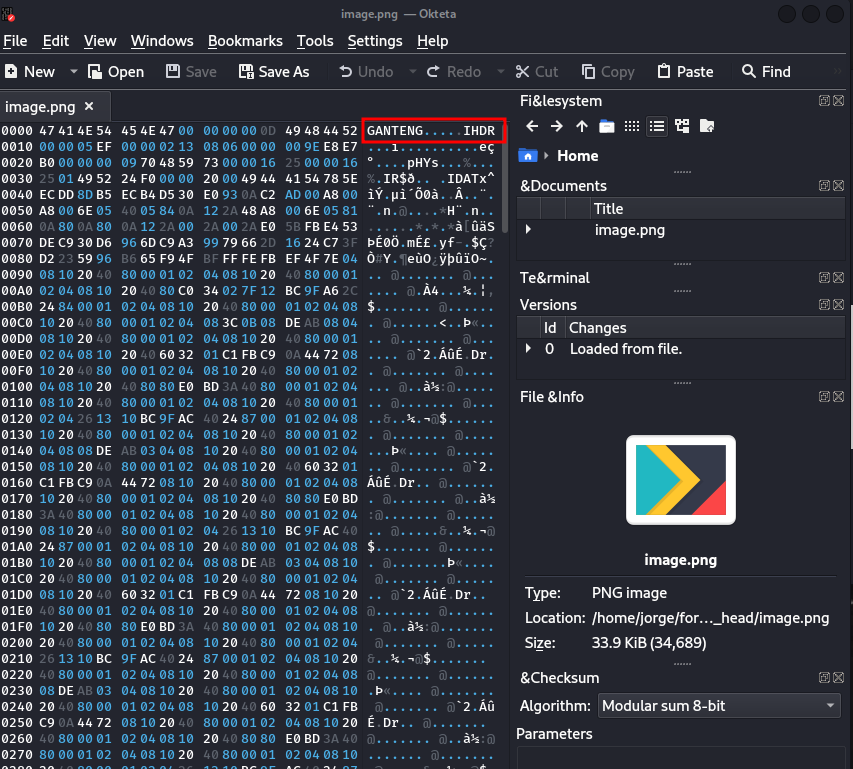
When we open the file, we can note that it has the words “GANTENG” and “IHDR”. In normal circumstances, the first few bytes of a file should indicate the file’s format. For instance, .gif animation files start with the string GIF89A.
If we search for “GANTENG”, we won’t find that it’s a file format. We’ll find that it means “handsome” in Indonesian. However, if we search for “IHDR”, we’ll find that it’s part of a png file header. The following is how a PNG file’s header’s sequence of bytes should be.
[00000000] 89 50 4E 47 0D 0A 1A 0A 00 00 00 0D 49 48 44 52 .PNG........IHDR
Our hypothesis right now is that we are dealing with a PNG file with a wrong header. Let’s use Okteta to modify our file so that it has the correct header.
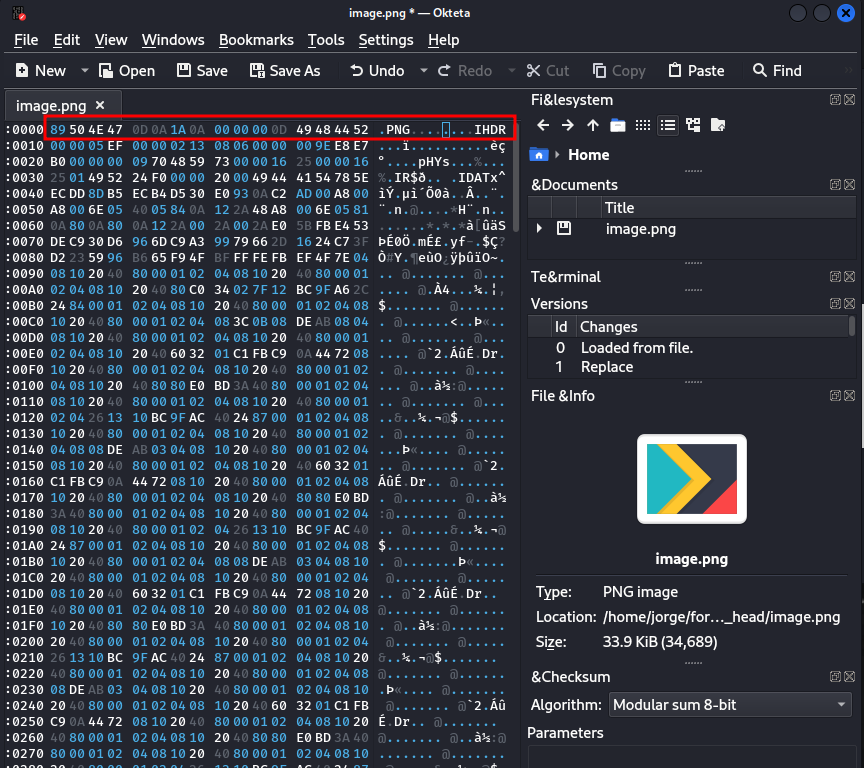
After modifying our file we can save a copy using File > Save As. If we did it correctly, we should have obtained a PNG file that we could open.
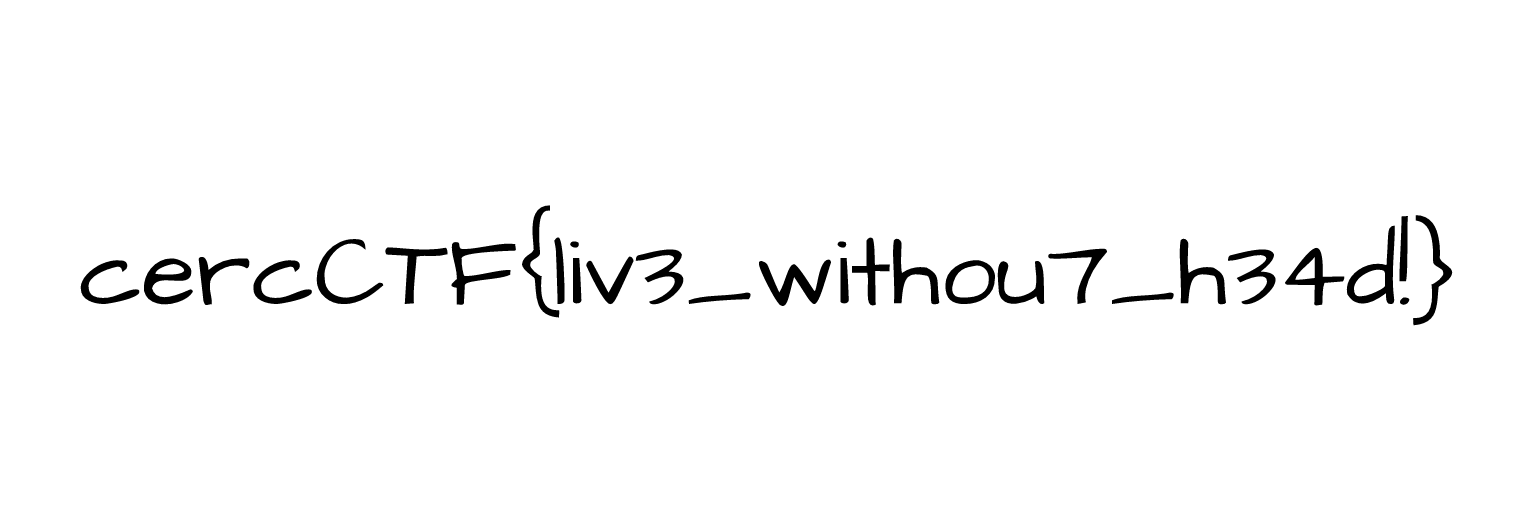
Nice! The image contains the flag.
The flag is: cercCTF{liv3_withou7_h34d!}
Challenge 9
Challenge 9 is called data format and it contains a file called tokiku.zip. Let’s make sure that the file is a zip as it claims to be.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/09_data_format]
└─$ file tokiku.zip
tokiku.zip: Zip archive data, at least v1.0 to extract, compression method=store
Good! We are dealing with a zip file. However, zip files are not always what they seem to be. For instance, Java applications are usually packed as .jar files, which are zip files with a specific internal structure. Open Document Format files i.e. .docx and .xlsx are also zip files.
We also need to keep in mind that Android apps are packed as .apk files which are also zip files.
Let’s decompress our file to analyze what we find.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/09_data_format]
└─$ unzip tokiku.zip
Archive: tokiku.zip
creating: app/
...
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/09_data_format]
└─$ ls
app gradle gradlew settings.gradle
build.gradle gradle.properties gradlew.bat tokiku.zip
After extracting the files, we can note that we have an app directory and some other files. If we search online, we’ll find that our structure corresponds to an Android application source, not an apk file.
Android’s documentation states that inside the app directory, we’ll find the source. As part of the source, we’ll find the java directory which contains the application source, and the res directory which contains resources such as images or string values.
If we search around the res directory, we’ll find a file called secret.xml. Let’s open it.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/09_data_format]
└─$ cat app/src/main/res/top-secret/secret.xml
<?xml version="1.0" encoding="utf-8"?>
<quest no="9">
<entry>
XML Content Top Secret
</entry>
<content>
<flag>Y2VyY0NURnt4bTFfaW5fZDNwN2h9</flag>
</content>
</quest>
We seem to be close because the XML file has a node called flag. However, it’s encoded. Just like before, we could have used Cyberchef. However, in this case, we can be sure that we are dealing with Base64 encoding. Let’s use the base64 command to recover our flag.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/09_data_format]
└─$ echo "Y2VyY0NURnt4bTFfaW5fZDNwN2h9" | base64 -d
cercCTF{xm1_in_d3p7h}
Great! We have our flag.
The flag is: cercCTF{xm1_in_d3p7h}
Challenge 10
This challenge is called gid. We’re provided with a file called deep_in_depth.zip. First, we’ll verify if the extension matches the file contents, and then we’ll create a directory called analysis to extract it there.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/10_gid]
└─$ file deep_in_depth.zip
deep_in_depth.zip: Zip archive data, at least v1.0 to extract, compression method=store
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/10_gid]
└─$ mkdir analysis
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/10_gid]
└─$ cp deep_in_depth.zip analysis
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/10_gid]
└─$ cd analysis
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/10_gid/analysis]
└─$ unzip deep_in_depth.zip
Archive: deep_in_depth.zip
creating: .git/
creating: .git/logs/
creating: .git/logs/refs/
creating: .git/logs/refs/heads/
inflating: .git/logs/refs/heads/master
...
From the output of the unzip command, we can note that we are dealing with a git repository. Git is a version control system that allows us to maintain the history of our files making it easy to roll back if it’s necessary.
Let’s list all the files. We want to make sure there’s nothing hidden.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/10_gid/analysis]
└─$ ls -lah
total 128K
drwxr-xr-x 3 jorge jorge 4.0K Mar 22 22:04 .
drwxr-xr-x 3 jorge jorge 4.0K Mar 22 22:01 ..
drwxr-xr-x 8 jorge jorge 4.0K Oct 30 2019 .git
-rw-r--r-- 1 jorge jorge 107K Mar 22 22:01 deep_in_depth.zip
-rw-r--r-- 1 jorge jorge 453 Oct 30 2019 index.html
It seems our flag should be in the index.html file. Let’s use cat index.html to explore its contents.
<!DOCTYPE html>
<html>
<head>
<title>CERC Teknik Komputer</title>
</head>
<body>
<h1 class="title-head">Hello, Selamat Datang di Challenge GIT!</h1>
<div class="container-fluid">
<p class="text-danger">Oops</p>
<table>
<tr>
<td>Noo</td>
<td>is it? b1n1e2hktg638moyl94ldsvjy2va1p</td>
</tr>
<tr>
</tr>
</table>
</div>
</body>
</html>
It seems the flag should be inside the table. However, this particular commit does not have the flag. We’ll need to check every version of this file. First, let’s check how many versions of this file there are with the git log command.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/10_gid/analysis]
└─$ git log
commit e6a21ed939499e9de4b2aefb22621fe86194fd4c (HEAD -> master)
Author: fannyhasbi <[email protected]>
Date: Wed Oct 30 13:44:08 2019 +0700
0zl4lp
commit 32b4d0782b149d1a4c2699c31e4e9375601323c7
Author: fannyhasbi <[email protected]>
Date: Wed Oct 30 13:44:08 2019 +0700
t3u7h4
commit c271cbbb31b65c3523656961b30031cb7c6cce4b
Author: fannyhasbi <[email protected]>
Date: Wed Oct 30 13:44:08 2019 +0700
m4ikbo
commit a54a43706beb9ae2c8eb6ac475cf8d6016778d3f
Author: fannyhasbi <[email protected]>
Date: Wed Oct 30 13:44:08 2019 +0700
inmk0c
commit 6baf014c33e54654423828a78289568279a76fc3
Author: fannyhasbi <[email protected]>
...
It seems there are way too many versions, so searching it manually would take a long time. Let’s automate it.
We’ll create a file called find_flag.sh with the following contents:
git rev-list --all | (
while read revision; do
git grep -F 'cerc' $revision
git grep -F '<td>' $revision
done
)
Our script queries for every commit of the repo, and then uses git grep to search for either the flag structure or for a table cell. Let’s run it.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/10_gid/analysis]
└─$ ./find_flag.sh
e6a21ed939499e9de4b2aefb22621fe86194fd4c:index.html: <td>Noo</td>
e6a21ed939499e9de4b2aefb22621fe86194fd4c:index.html: <td>is it? b1n1e2hktg638moyl94ldsvjy2va1p</td>
32b4d0782b149d1a4c2699c31e4e9375601323c7:index.html: <td>Noo</td>
32b4d0782b149d1a4c2699c31e4e9375601323c7:index.html: <td>is it? 5bw6ojed9p231772npod822227wamm</td>
c271cbbb31b65c3523656961b30031cb7c6cce4b:index.html: <td>Noo</td>
c271cbbb31b65c3523656961b30031cb7c6cce4b:index.html: <td>is it? lgigjs99ufbbn4uw4bc4f8cbcqbn3e</td>
a54a43706beb9ae2c8eb6ac475cf8d6016778d3f:index.html: <td>Noo</td>
a54a43706beb9ae2c8eb6ac475cf8d6016778d3f:index.html: <td>is it? 7390xf8ilws167ud4ktrqjyd3awjp9</td>
6baf014c33e54654423828a78289568279a76fc3:index.html: <td>Noo</td>
6baf014c33e54654423828a78289568279a76fc3:index.html: <td>is it? t82s57i1b1pjjx0qrw17zkhr8u5a5t</td>
6c12878c2b1d649dd4692c65b42d35d0506384bf:index.html: <td>Noo</td>
6c12878c2b1d649dd4692c65b42d35d0506384bf:index.html: <td>is it? hmgauinejq0t2rwiqe9z95nk5oeeh1</td>
f8a4c44103023f2aa6d4ae245172be8cc504410d:index.html: <td>Noo</td>
f8a4c44103023f2aa6d4ae245172be8cc504410d:index.html: <td>is it? ob33ixhv12gxmlzfhcccvonmmwkgay</td>
cb87386bf0dfccd30a0a5ca48b94d2fc3db43920:index.html: <td>Noo</td>
cb87386bf0dfccd30a0a5ca48b94d2fc3db43920:index.html: <td>is it? x1dbfbseasj65wlf1evzyctdd9sb7z</td>
a3950a400f91d588c133390590e748a1be303d22:index.html: <td>Noo</td>
a3950a400f91d588c133390590e748a1be303d22:index.html: <td>is it? 7m8ku6hks9wzpb43was7rqr1aq2c3j</td>
31666e8ac62e50463a67c83f7a954459342e43d9:index.html: <td>Noo</td>
31666e8ac62e50463a67c83f7a954459342e43d9:index.html: <td>is it? 3rh88wthhw5hljytnwwfkgj1n7bj6r</td>
82489335c66103cc2c4cb63c018e266353ee01dc:index.html: <td>Noo</td>
82489335c66103cc2c4cb63c018e266353ee01dc:index.html: <td>is it? hxbejzotldkk1nsuj55i3nf4a6ipqw</td>
49ca147defea25b21b7be05ae0d567169d78a61d:index.html: <td>Noo</td>
49ca147defea25b21b7be05ae0d567169d78a61d:index.html: <td>is it? 2lwu5imy5osrfhentgslfn564a8nsr</td>
25d75d792e60545e6fbbb2fd01ec7a6084aef818:index.html: <td>Noo</td>
25d75d792e60545e6fbbb2fd01ec7a6084aef818:index.html: <td>is it? q6e5uvo7uq49up7z8yuxiwnzlqmjoa</td>
b64afd824d7a96949d3efed99f31b6525f764272:index.html: <td>Noo</td>
b64afd824d7a96949d3efed99f31b6525f764272:index.html: <td>is it? cgecfo1ct5alo9fiyuimhwuv8mv463</td>
0a6f14fb0a23031e75e79899cf67e3e201308e42:index.html: <td>Noo</td>
0a6f14fb0a23031e75e79899cf67e3e201308e42:index.html: <td>is it? cfmcw7bw154w5v4muc4djw7rasvylg</td>
0fb3338c36664a7d80548b4f18e0ce70150d3c4a:index.html: <td>Noo</td>
0fb3338c36664a7d80548b4f18e0ce70150d3c4a:index.html: <td>is it? ztk9lotwyz7dck6ak048c14y6zm72x</td>
3c44026ffdc0d23bef453bd5bcfc13284726cc4c:index.html: <td>Noo</td>
3c44026ffdc0d23bef453bd5bcfc13284726cc4c:index.html: <td>is it? 2ef9zeyjyycenfquz2cpq4lgmid3jx</td>
d616ad391894d42ede3d79f9ea3993854cdf05f9:index.html: <td>rla0zvjc6gqtdtt2c86zuasubwdkzi</td>
69fd2d5fcd12726c1bc1fbeb755d1c8bc1383c5f:index.html: <td>44vpd1hcg9fnlh1ruo4g3b1t7uj2xa</td>
f7a208f86f2e847a278e7805d283329530d5e966:index.html: <td>y8hj0xrdvit45v8bi5psn6st0grwax</td>
728b9147e12b8a7c15d5fffde7c3855da7ad908b:index.html: <td>c9glpig5zk98epusnan2nj1340cqp9</td>
9093618387b19877f8f4ec5819c2832d0e98e1e9:index.html: <td>vcaa1byh70n72pc4b9rrop1uwrypjp</td>
052660830af07112d62dc2e2cea5af8e937a4cfc:index.html: <td>6bf8a9zczb6k86sd7nu6spr7cdx4bp</td>
a14849c86a486a3cd9a41bcd546db1961519e54b:index.html: <td>8042sl44a5sz85xqsh30eafd42nhbh</td>
73ada71acecaebc1e57f7a9a0ab51b412bcf092a:index.html: <td>sck65u3vpdj7exyxwx4hfz33attagt</td>
5cc9e40a0c2a3296ec589447b381c1bc4101e376:index.html: <td>jktf46tioqirm354v4lkcqtt1nd7bv</td>
372eb3b7aa968520c475fd9306df9c4c843fa289:index.html: <td>3urd66knioke5ri61z975l957aj5oj</td>
f30773a9b4ac6038527f3d7f1ff8ce1463655b52:index.html: <td>the right one : MNSXEY2DKRDHWZZRG5PWS3S7MQZTG4D5BI======</td>
4a7407a36d268f3a7f3c3813d4a8a755d92daec5:index.html: <td>FLUG[huhuhu]</td>
405639cceb438853dae3e700ca425a98e982ff00:index.html: <td>FLUG[huhuhu]</td>
9bd7dbd8af6a072029d67150b02176948510221a:index.html: <td>FLUG[huhuhu]</td>
155137df5ff29b0bd59b2b180da70ad7349e2241:index.html: <td>FLUG[huhuhu]</td>
5dd3c45e5afae262b3d7353981309f741e369fec:index.html: <td>FLUG[huhuhu]</td>
4f39dc6795f3c6250b021eb16d91e93788bbcdf8:index.html: <td>FLUG[huhuhu]</td>
fabc939ee574869ce33299e8c5b8c1eb1e35ece7:index.html: <td>FLUG[huhuhu]</td>
bccbe705d25526cc1b6cb4848795cd77b4c1e555:index.html: <td>FLUG[huhuhu]</td>
e8e9485ba99430a6ea1fc7bdf94fe4082d9327ff:index.html: <td>FLUG[huhuhu]</td>
dab336aa5f60313c2a3bbf6c1ee5d292c243cabf:index.html: <td>FLUG[huhuhu]</td>
5d37f30ece8226901f1b58f054e351abed831027:index.html: <td>y1d8miuq73fvaujffyvx</td>
dcefe936b995ab794f3443942cd444c7561644f8:index.html: <td>a426tgv4p5pqtfnj0vxy</td>
eaea32f52f42f48f8c159d395e57b2d5f2d4e62b:index.html: <td>aflbva03kv4zdptcyobd</td>
64d8b67ff905fdc8c6244bbf473f1532a3fb8b3d:index.html: <td>qiddfxx4zbjcg3vweku0</td>
aca5c9690e2451acdc9a6bb3e48a383a85c8f447:index.html: <td>44jyxpnpdyacrcac8ctd</td>
b9831355a5906c4e753b269c19cf8709dd74d4b7:index.html: <td>14wvxunsngzidbfmltom</td>
ee01dafe88dddd77d9cce3198cfebcb425599016:index.html: <td>ab918o3xuhwn4278fetc</td>
7cde2a0451307ddc749a8ec2bcccb2dd50260639:index.html: <td>odq8z44k5w2vtwq5yldj</td>
e0cb3cc3983d7961d04d3c50a1f001e26ada02a4:index.html: <td>2ohtek8bxsf8f5jcospz</td>
8d79add703944b527ce9723c2c21481c7e9bbabe:index.html: <td>ufxl2ilufhl50uoavn14</td>
61ef51c911383701cb1e45e52841f399148b4a36:index.html: <td>Flag{FAHMI WAS HERE}</td>
24197ec2746da837b7f0309c4187315a3bb667b4:index.html: <td>Flag{MANA FLAGNYA B*D*HHHH}</td>
ccb352fcfd24479d1f21374559448778a40486fb:index.html: <td>Flag{FLAG INI DICURRY TEAM b333f}</td>
2d9021dbe08fc10e87dd2f62edc93622cbf4de2e:index.html: <td>Flag{GEMASTHICC13 HOSTNYA BUKAN UNDEP JADI INI BUKAN FLAGNYA}</td>
d923071e5edd15072b6b9394cef6fc2248ba535b:index.html: <td>Flag{SAYYID AMBIL FLAGNYA}</td>
58bdb32720b0ef32545d312fec8601aa1e55d831:index.html: <td>Flag{stolen}</td>
ca641e823fd20992982d8e73c5afaa82f49ae285:index.html: <td>Flag{hmmm__apayaaaaa}</td>
574e8689754da53f6f136216c6656dae92209e11:index.html: <td>Flug{turuq}</td>
52dad229f66c05315224c2d2053f745af18d769d:index.html: <td>Flug</td>
0a552520683e6e48677b4b60981e59abfd7fbb2a:index.html: <td>Flag</td>
7e79e1e545451217cbb623053765f448242b8f04:index.html: cercCTF{######}
7e79e1e545451217cbb623053765f448242b8f04:index.html: <td>Flag</td>
Even after executing our script, we have many results to check. However, there’s an interesting one:
f30773a9b4ac6038527f3d7f1ff8ce1463655b52:index.html: <td>the right one : MNSXEY2DKRDHWZZRG5PWS3S7MQZTG4D5BI======</td>
This entry says “the right one”. Again, we can use Cyberchef to analyze the string, and if we do , we’ll find that we’re dealing with Base32 encoding.
Nice! Decoding that string provided us with the flag.
The flag is: cercCTF{g17_in_d33p}
That’s it for now. We’ve solved challenges from 6 to 10. We’ve learned a few grep tricks, how to traverse a git repo to find a particular string, and also how to modify a file using a hex editor.
We’ll continue in part 3 .