Forensics Beginner Challenges Part 1 of 3
- Jorge Morán
- Ctf , Forensics
- March 22, 2024
- 5 min
The other day I was looking for some forensics beginner exercises. I found a few, but a particular repo caught my eye because the repo itself didn’t contain the answers. Shoutout to CERC Undip for the fun repo with 16 challenges. I also created a fork just in case it’s ever deleted.
According to the README, we should be able to solve everything without using too many tools. All of them are available in Kali, so that’s what I’m going to use. Without further ado, let’s start with the challenges.
Challenge 1
The first challenge’s file is called simple_af.png. We can get the flag just by opening the file.
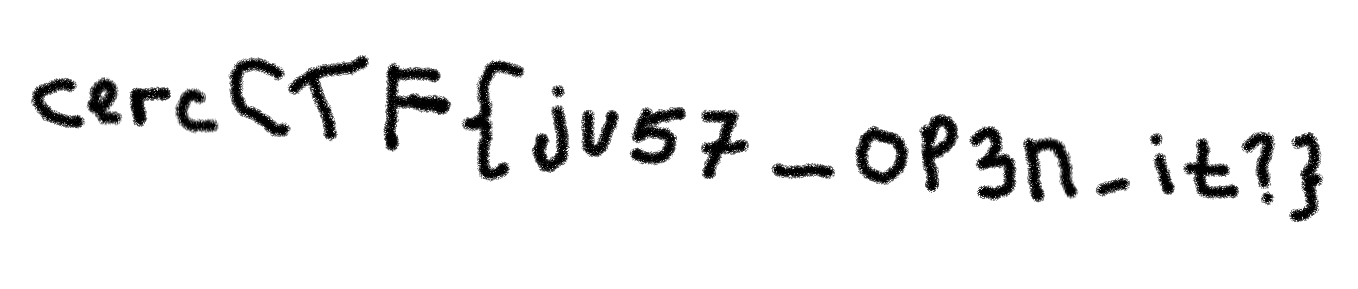
The flag is: cercCTF{ju57_op3n_it?}
Challenge 2
This challenge has another image named h3re.jpg. If we open it as an image, we won’t find anything related to the flag we are looking for. Since it’s an image, our first option should be to check for EXIF data. EXIF is a type of metadata that images contain. The typical uses of EXIF are GPS tags or additional comments related to the picture. Let’s investigate if that’s where the flag is.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/02_string]
└─$ exiftool h3re.jpg
ExifTool Version Number : 12.76
File Name : h3re.jpg
Directory : .
File Size : 18 kB
File Modification Date/Time : 2024:03:20 22:18:44-05:00
File Access Date/Time : 2024:03:22 20:48:19-05:00
File Inode Change Date/Time : 2024:03:20 22:18:44-05:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Image Width : 236
Image Height : 342
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 236x342
Megapixels : 0.081
From the output, we can note that nothing resembles the flag structure of the first challenge. Let’s investigate some more. Maybe this image has another file concatenated to it. To verify this, we can use binwalk
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/02_string]
└─$ binwalk h3re.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
Binwalk indicates that this is only an image. So when all else fails, let’s use strings to find anything that resembles an ASCII string within the file, and then we can grep for the flag structure (it should start with cercCTF).
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/02_string]
└─$ strings h3re.jpg | grep "cercCTF"
cercCTF{s1mpl3_i5_fum}
Nice! We found the flag.
The flag is: cercCTF{s1mpl3_i5_fum}
Challenge 3
This challenge has a file called whats_th1s. What’s interesting about this file is that it doesn’t have an extension. First, let’s use the file command to get an idea of the file’s content, and then let’s apply the right extension. We’ll later analyze if that works.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/03_no_ext]
└─$ file whats_th1s
whats_th1s: PNG image data, 1847 x 281, 8-bit/color RGBA, non-interlaced
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/03_no_ext]
└─$ mv whats_th1s whats_th1s.png
According to the file command, we’re dealing with another image. So now that we changed its extension, we can try to open it as an image.
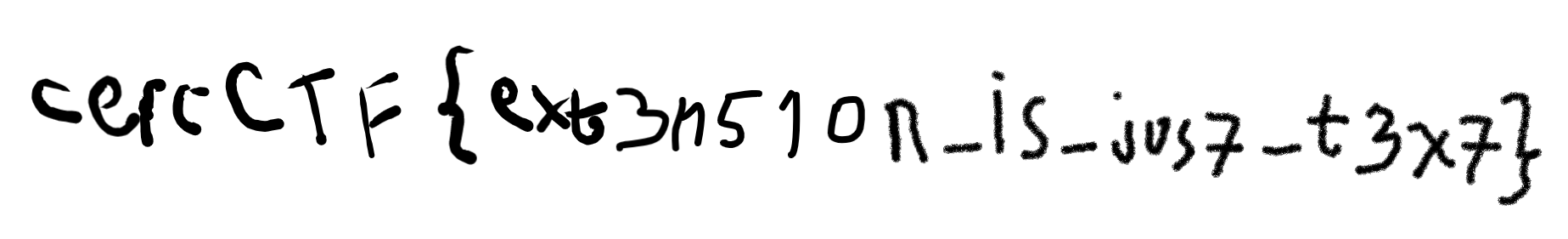
The flag is: cercCTF{ext3n51on_1s_jus7_t3x7}
Challenge 4
This challenge has a file called file.docx. We can follow the same procedure as the previous challenge. If the file command says we are dealing with another type of file, we’ll just change the extension and try opening it.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/04_ext]
└─$ file file.docx
file.docx: PNG image data, 2042 x 196, 8-bit/color RGBA, non-interlaced
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/04_ext]
└─$ mv file.docx file.png
It seems we are once again dealing with an image. Let’s try to open it.

The flag is: cercCTF{onc3_wrong_do5n7_m34n_wrong}
As challenges 3 and 4 have shown us. Extensions mean nothing, it’s the content of a file what defines how we should open it.
Challenge 5
The fifth challenge contains a file called creeeeepieeee.wav. To tackle this one, we’ll first verify if this is indeed an audio file. If it is, we could check if the audio file contains metadata with the exiftool command.
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/05_meta]
└─$ file creeeeepieeee.wav
creeeeepieeee.wav: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, stereo 44100 Hz
┌──(jorge㉿eternatus)-[~/forensics/forensic-beginner-challenges/05_meta]
└─$ exiftool creeeeepieeee.wav
ExifTool Version Number : 12.76
File Name : creeeeepieeee.wav
Directory : .
File Size : 1627 kB
File Modification Date/Time : 2024:03:20 22:18:44-05:00
File Access Date/Time : 2024:03:22 21:17:48-05:00
File Inode Change Date/Time : 2024:03:20 22:18:44-05:00
File Permissions : -rw-r--r--
File Type : WAV
File Type Extension : wav
MIME Type : audio/x-wav
Encoding : Microsoft PCM
Num Channels : 2
Sample Rate : 44100
Avg Bytes Per Sec : 176400
Bits Per Sample : 16
Date Created : 2007:01:18
Software : Lavf58.29.100 (libsndfile-1.0.28)
ID3 Size : 158
User Defined Text : (Software) Lavf58.29.100
Artist : Orang Ganteng Tekkom
Recording Time : 2007:01:18
Comment : Y2VyY0NURntleDFmX21ldGFfNHJlX2ZydTMzbmR6enp9Cg==
Date/Time Original : 2007:01:18
Duration : 9.22 s
The extension of the file was right. Also, within the metadata, there’s a comment that appears interesting:
_Y2VyY0NURntleDFmX21ldGFfNHJlX2ZydTMzbmR6enp9Cg==_
The string corresponds to a base64 encoded string. If we didn’t know that, we could have used CyberChef with its “magic” recipe
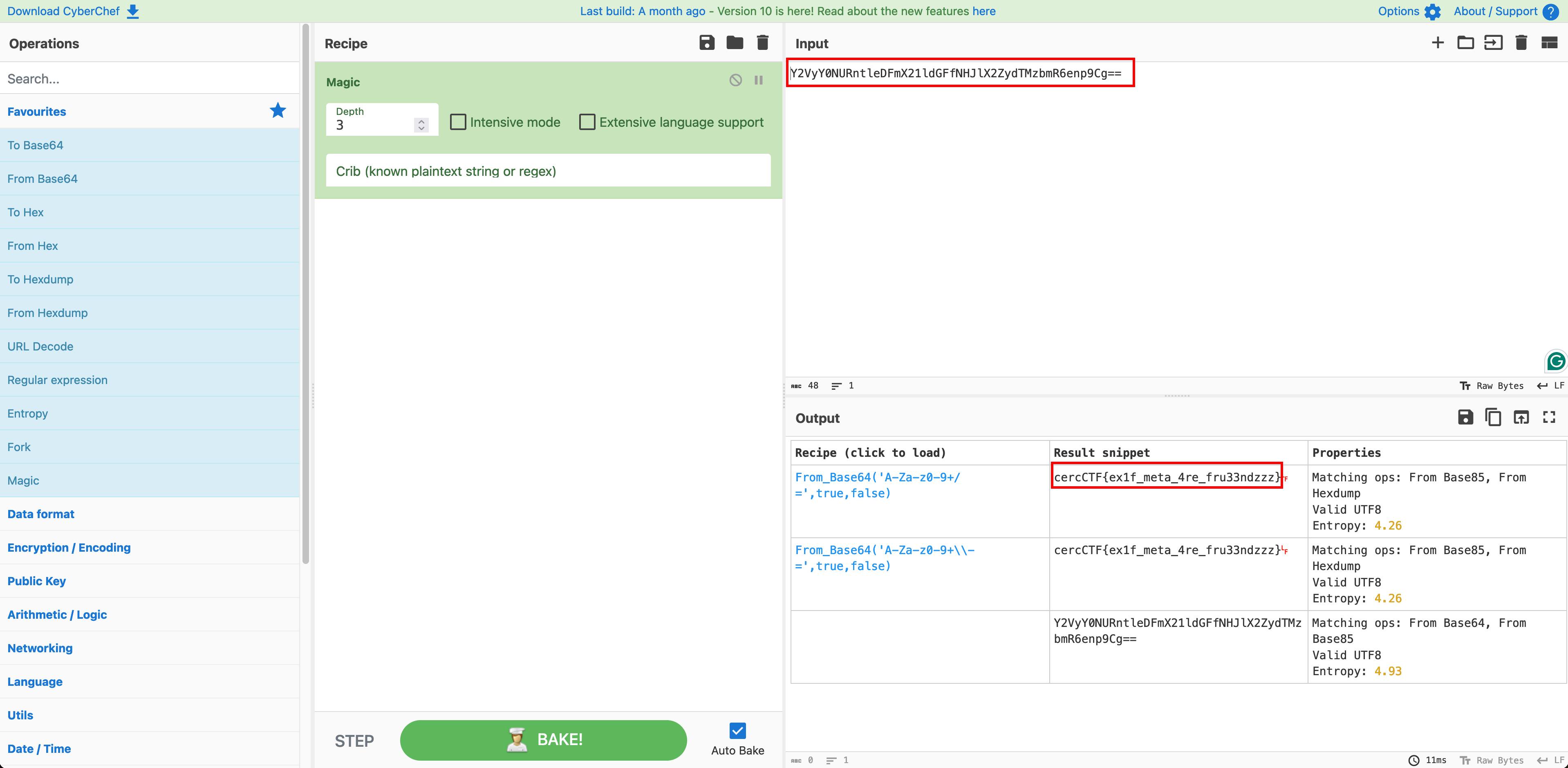
Cyberchef’s magic recipe gave us an idea of what the encoding of the text is and even provided us with the flag.
The flag is: cercCTF{ex1f_meta_4re_fru33ndzzz}
That’s it for now. We’ve solved challenges from 1 to 5. We’ve learned about how unimportant file extensions are, and also about file metadata as a way to find additional information about a file.
We’ll continue in part 2 .